什么是JWT?
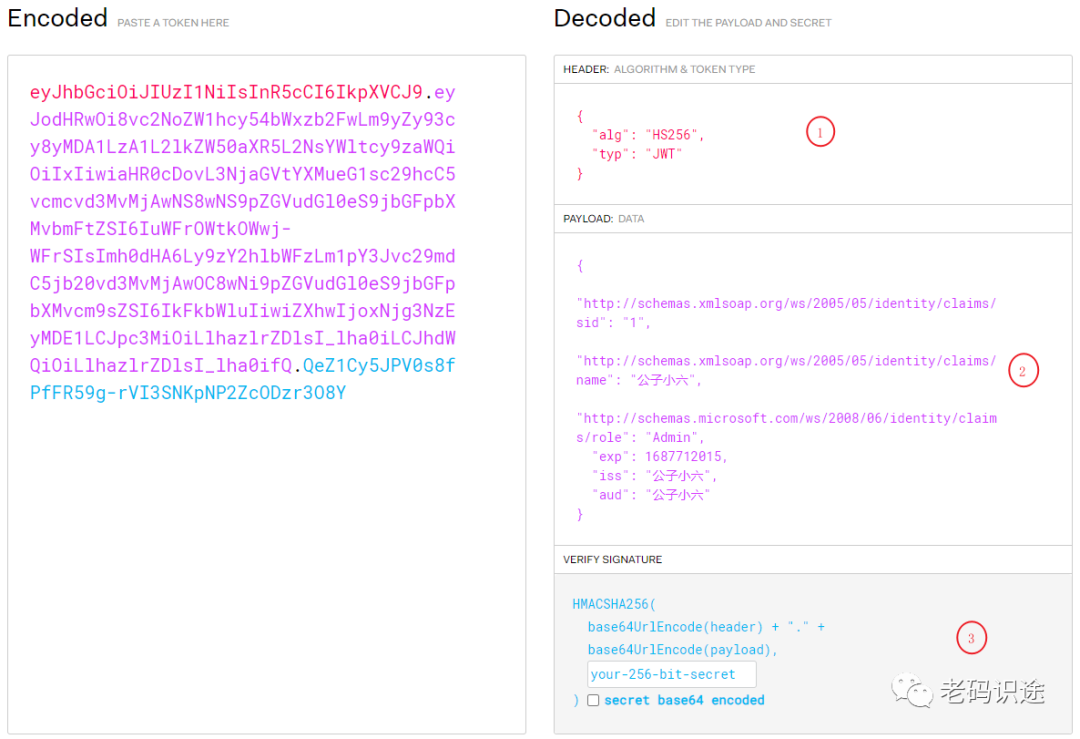
JWT组成
-
头信息指定了该JWT使用的签名算法,
HS256表示使用了 HMAC-SHA256 来生成签名。 -
消息体包含了JWT的意图
-
未签名的令牌由
base64url编码的头信息和消息体拼接而成(使用"."分隔),签名则通过私有的key计算而成。 -
最后在未签名的令牌尾部拼接上
base64url编码的签名(同样使用"."分隔)就是JWT了 -
典型的JWT的格式:xxxxx.yyyyy.zzzzz
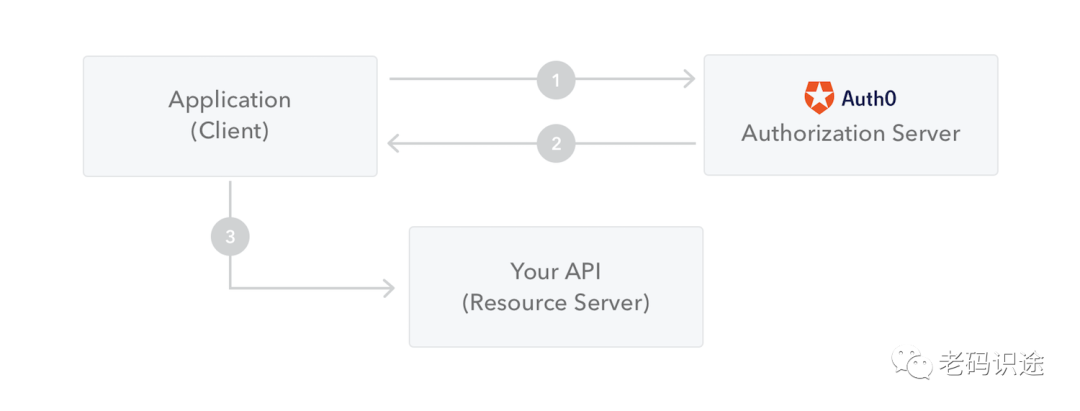
应用JWT步骤
builder.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme).AddJwtBearer(options =>{options.TokenValidationParameters = new TokenValidationParameters{ValidateIssuer = true,ValidateAudience = true,ValidateLifetime = true,ValidateIssuerSigningKey = true,ValidIssuer = TokenParameter.Issuer,ValidAudience = TokenParameter.Audience,IssuerSigningKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(TokenParameter.Secret))};});
app.UseAuthentication();app.UseAuthorization();
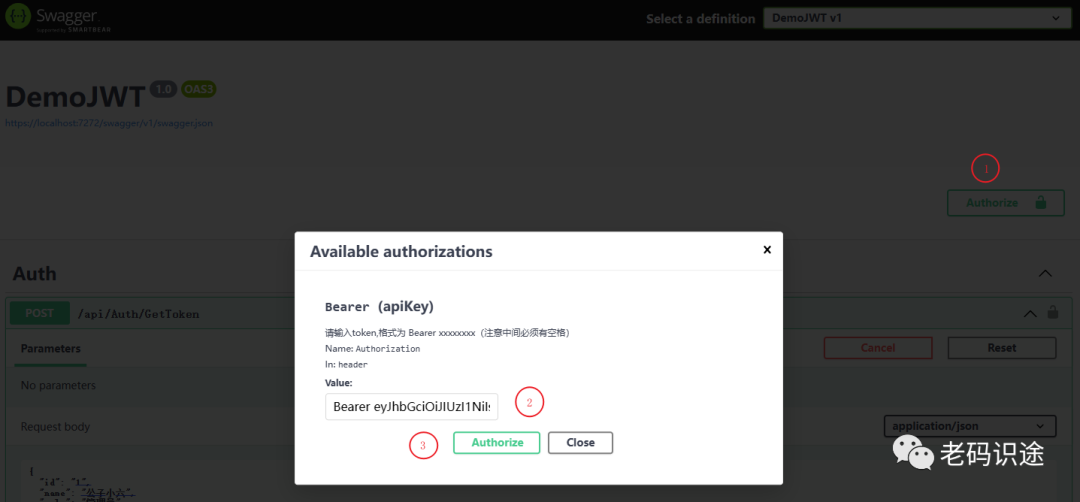
builder.Services.AddSwaggerGen(options =>{options.AddSecurityDefinition("Bearer", new OpenApiSecurityScheme{Description = "请输入token,格式为 Bearer xxxxxxxx(注意中间必须有空格)",Name = "Authorization",In = ParameterLocation.Header,Type = SecuritySchemeType.ApiKey,BearerFormat = "JWT",Scheme = "Bearer"});//添加安全要求options.AddSecurityRequirement(new OpenApiSecurityRequirement {{new OpenApiSecurityScheme{Reference =new OpenApiReference{Type = ReferenceType.SecurityScheme,Id ="Bearer"}},new string[]{ }}});});
using DemoJWT.Models;using Microsoft.AspNetCore.Authentication.Cookies;using Microsoft.IdentityModel.Tokens;using System.IdentityModel.Tokens.Jwt;using System.Security.Claims;using System.Text;namespace DemoJWT.Authorization{public class JwtHelper{public static string GenerateJsonWebToken(User userInfo){var securityKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(TokenParameter.Secret));var credentials = new SigningCredentials(securityKey, SecurityAlgorithms.HmacSha256);var claimsIdentity = new ClaimsIdentity(CookieAuthenticationDefaults.AuthenticationScheme);claimsIdentity.AddClaim(new Claim(ClaimTypes.Sid, userInfo.Id));claimsIdentity.AddClaim(new Claim(ClaimTypes.Name, userInfo.Name));claimsIdentity.AddClaim(new Claim(ClaimTypes.Role, userInfo.Role));var token = new JwtSecurityToken(TokenParameter.Issuer,TokenParameter.Audience,claimsIdentity.Claims,expires: DateTime.Now.AddMinutes(120),signingCredentials: credentials);return new JwtSecurityTokenHandler().WriteToken(token);}}}
namespace DemoJWT.Authorization{public class TokenParameter{public const string Issuer = "公子小六";//颁发者public const string Audience = "公子小六";//接收者public const string Secret = "1234567812345678";//签名秘钥public const int AccessExpiration = 30;//AccessToken过期时间(分钟)}}
using DemoJWT.Authorization;using DemoJWT.Models;using Microsoft.AspNetCore.Http;using Microsoft.AspNetCore.Mvc;using System.IdentityModel.Tokens.Jwt;namespace DemoJWT.Controllers{[Route("api/[controller]/[Action]")][ApiController]public class AuthController : ControllerBase{[HttpPost]public ActionResult GetToken(User user){string token = JwtHelper.GenerateJsonWebToken(user);return Ok(token);}}}
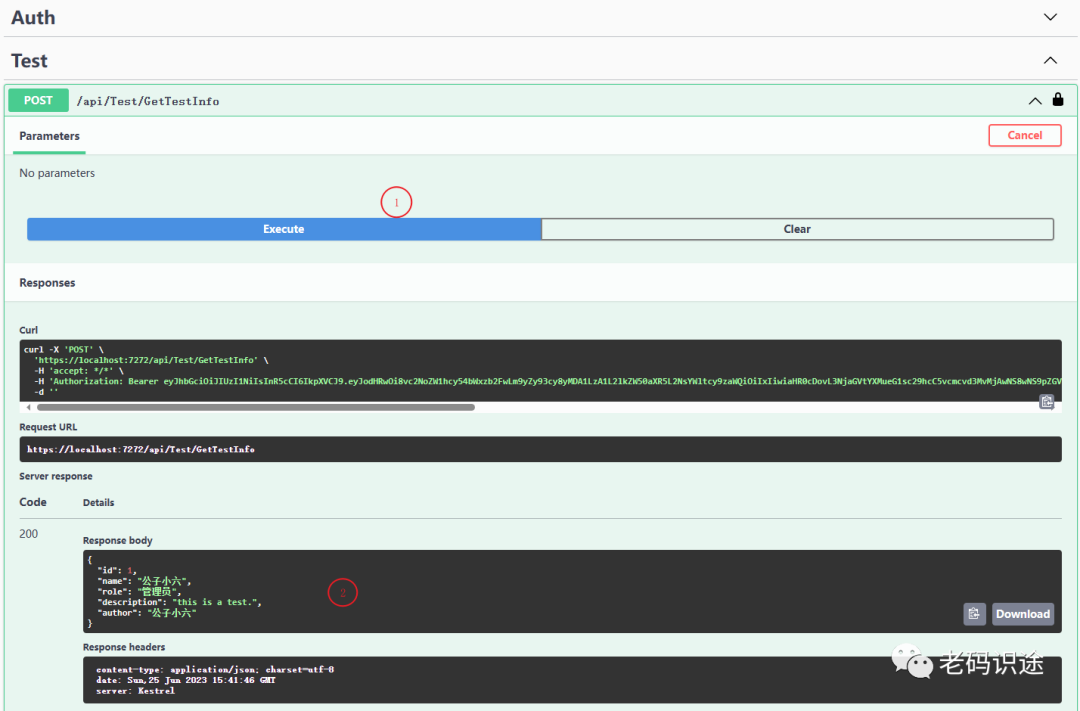
using DemoJWT.Models;using Microsoft.AspNetCore.Authorization;using Microsoft.AspNetCore.Http;using Microsoft.AspNetCore.Mvc;using System.Security.Claims;namespace DemoJWT.Controllers{[Authorize][Route("api/[controller]/[Action]")][ApiController]public class TestController : ControllerBase{[HttpPost]public ActionResult GetTestInfo(){var claimsPrincipal = this.HttpContext.User;var name = claimsPrincipal.Claims.FirstOrDefault(r => r.Type == ClaimTypes.Name)?.Value;var role = claimsPrincipal.Claims.FirstOrDefault(r => r.Type == ClaimTypes.Role)?.Value;var test = new Test(){Id = 1,Name = name,Role = role,Author = "公子小六",Description = "this is a test.",};return Ok(test);}}}
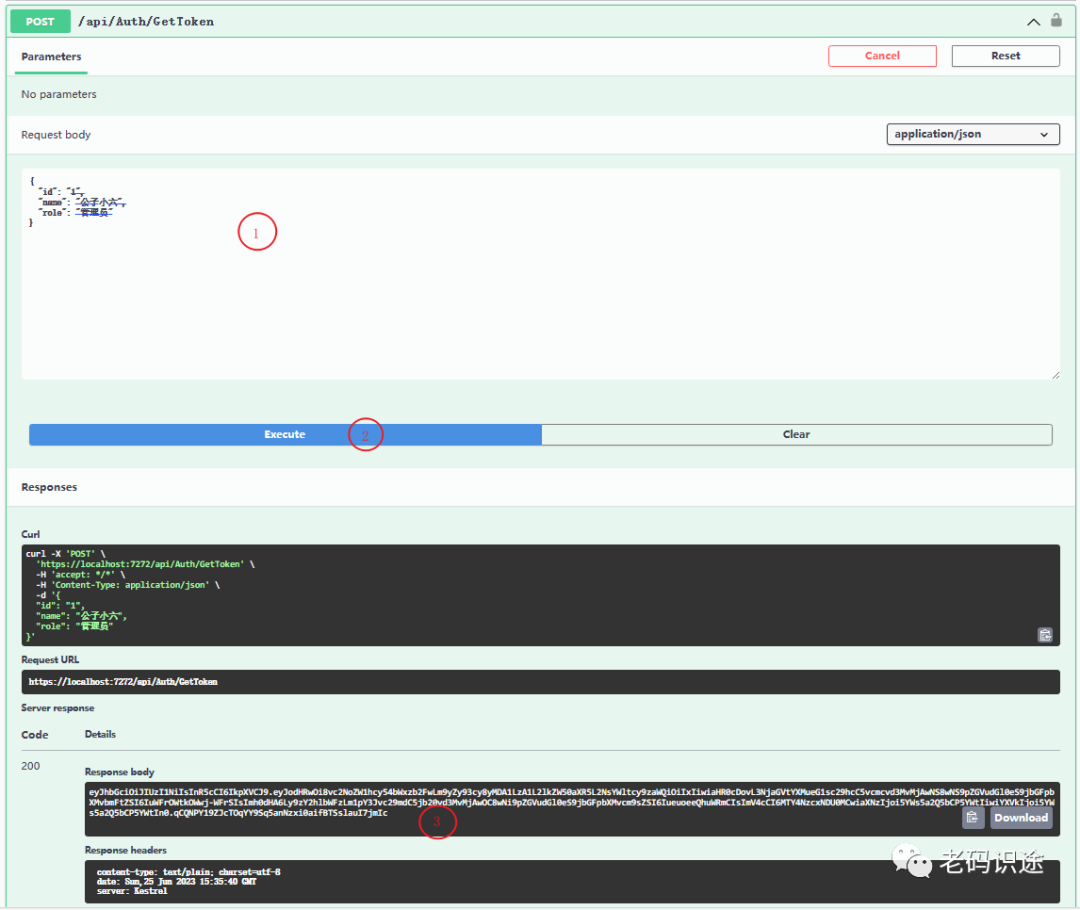
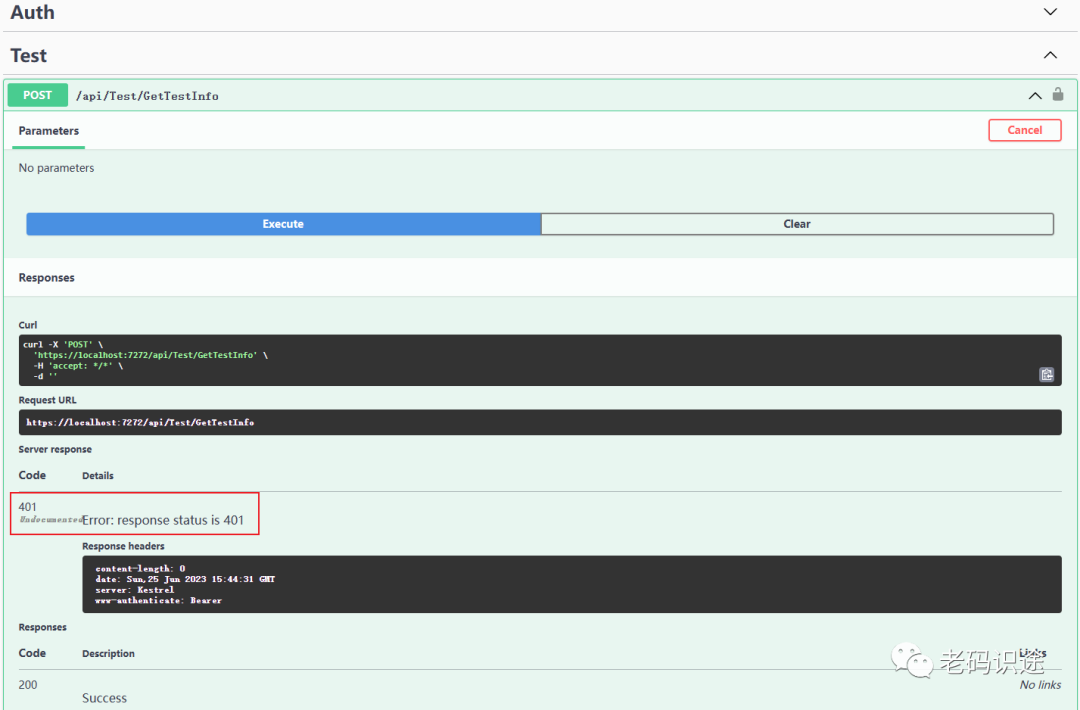
接口测试